Setup P2S Azure VPN with the integration of Azure AD SSO
Delve into a simple guide on integrating Azure AD Single Sign-On (SSO) with P2S Azure VPN. Enhance secure access and streamline user authentication with this straightforward setup.
In this tutorial, we will set up a P2S Azure VPN connection within our VNet. We will deploy the Azure Virtual network gateway and consider you have VNet created. If you don’t have a virtual network deployed, you can follow this documentation to do so https://learn.microsoft.com/en-us/azure/virtual-network/quick-create-portal
These are steps that are going to be covered in this tutorial for successfully deploying P2S Azure VPN with the integration of Azure AD SSO:
- Deploy Virtual network gateway
- Configure Virtual network gateway
- Test everything
Deploy Virtual network gateway
Search for Virtual network gateways and click “Create”

For the “SKU” option, you need to choose one of the following options, otherwise, your VPN won’t work: “VpnGw1”, “VpnGw2”, “VpnGw3”, “VpnGw4” or “VpnGw5”. Other variables you can populate upon your preferences and other settings you can leave the default.
Disclaimer: it takes around 45 minutes for the Virtual network gateway to be deployed
Configure Virtual network gateway
Once your Virtual network gateway is deployed, you need to configure it in order to have a properly working Azure AD SSO within your VNet. It contains 2 important parts:
- Authorize the Azure VPN application
- Configure Point-to-site configuration
1. Authorize the Azure VPN application
2. Configure Point-to-site configuration
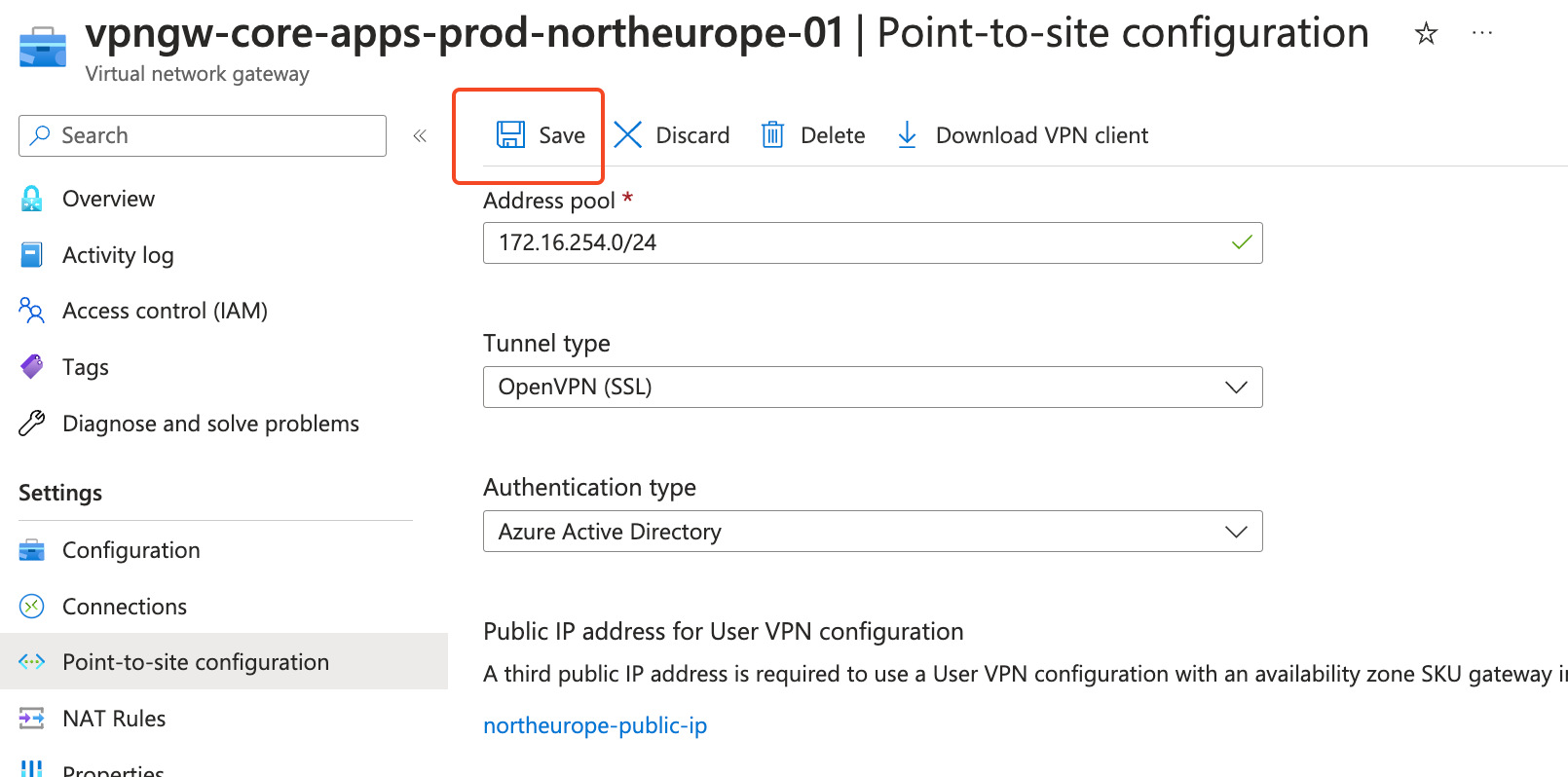
Go to your Virtual network gateway resource and click “Point-to-site configuration”
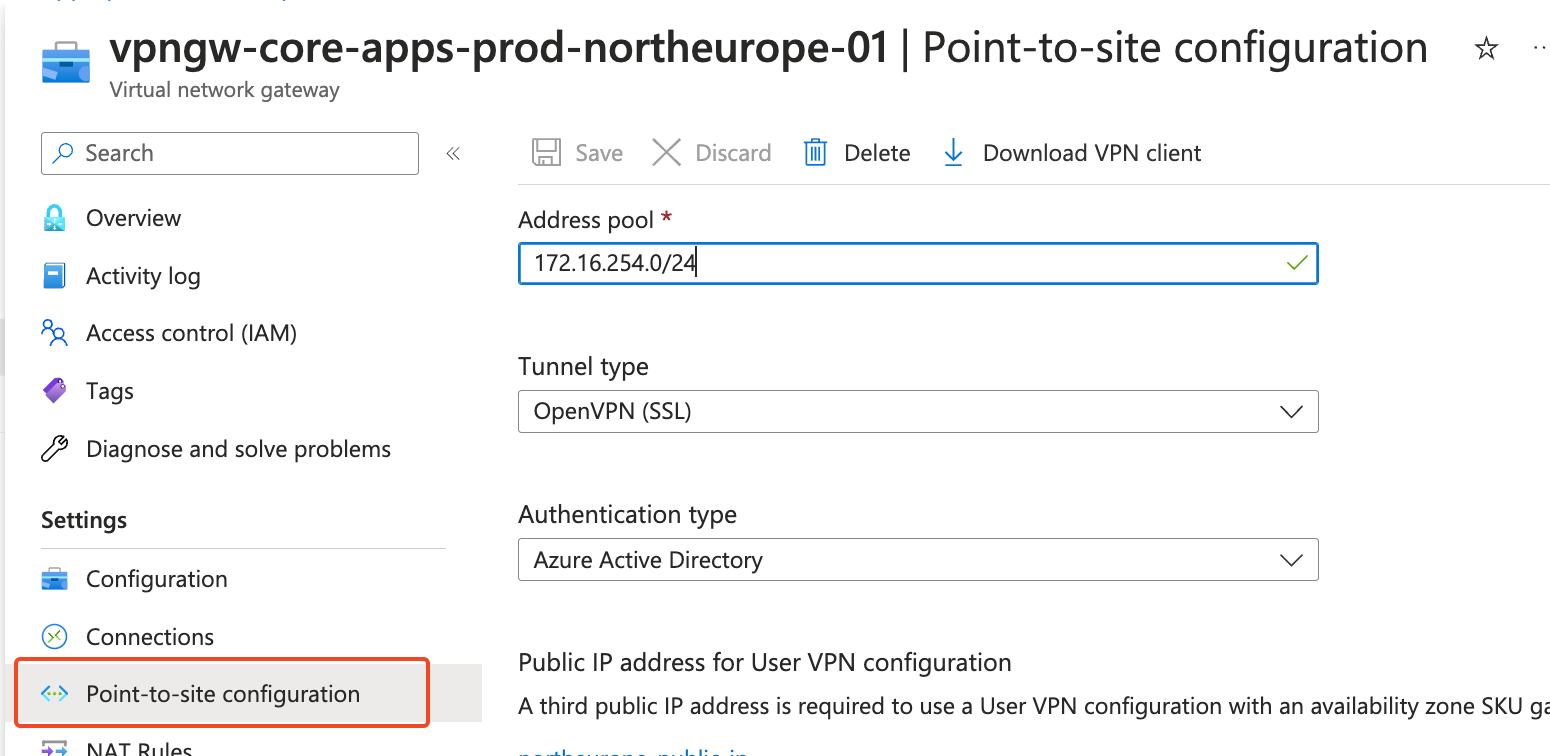
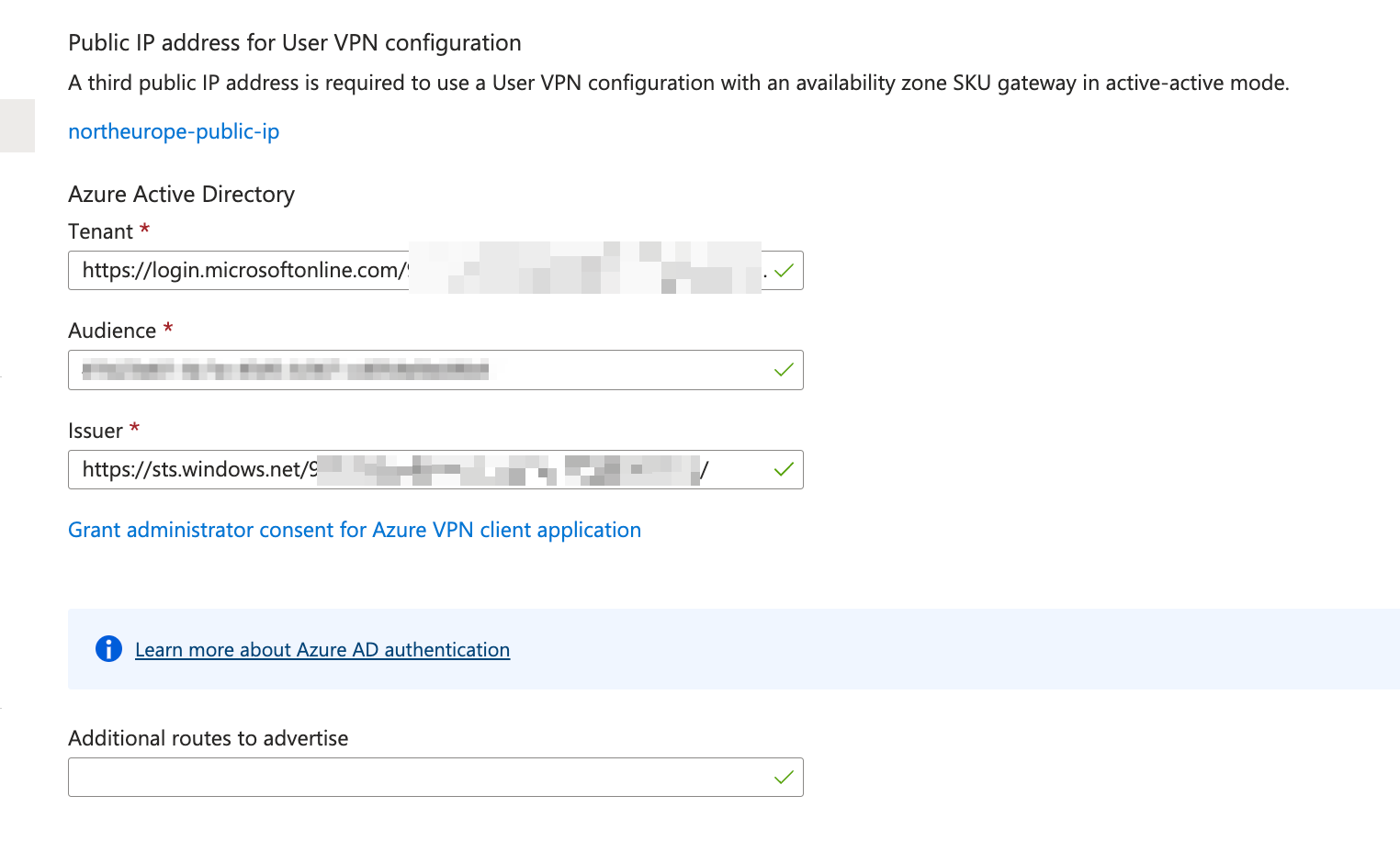
After successfully populating variables, click “Save”. Keep in mind this process will take around 15 minutes.
Test everything
You need to download the VPN client file, download the Azure VPN client and connect with the Azure VPN client.
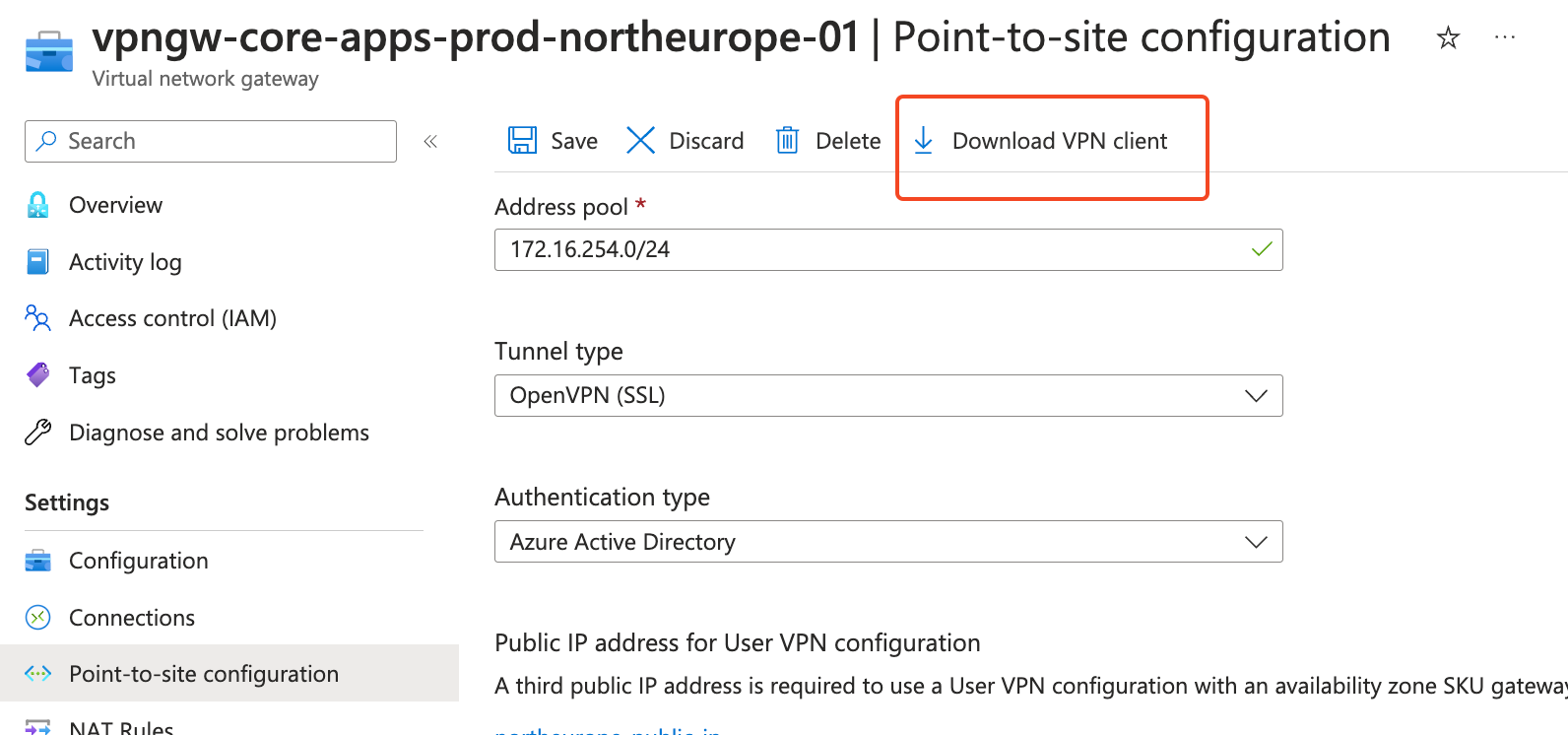
You can download the VPN client file by following the steps:
- go to your Virtual network gateway resource
- “Point-to-site configuration”
- “Download VPN client”
After that, download the Azure VPN client and connect to the network.
- For MacOS - follow this documentation https://learn.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-client-mac
- For Windows - follow this documentation https://learn.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-client
Useful links
- https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-point-to-site-resource-manager-portal
- https://learn.microsoft.com/en-us/azure/vpn-gateway/point-to-site-about
- https://learn.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-client
- https://learn.microsoft.com/en-us/azure/virtual-network/quick-create-portal
- https://learn.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpngateways
- https://learn.microsoft.com/en-us/azure/vpn-gateway/openvpn-azure-ad-tenant
- https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-how-to-find-tenant
- https://learn.microsoft.com/en-us/azure/active-directory/fundamentals/active-directory-access-create-new-tenant
- https://www.youtube.com/watch?v=Ur0WNjnXJrU
Facing Challenges in Cloud, DevOps, or Security?
Let’s tackle them together!
get free consultation sessions
We will contact you shortly.







